Before we get into the nitty-gritty: everyone knows that LAPS is free – what you might not know is that Admin By Request is also free, for 25 endpoints. Check it out here.
LAPS
LAPS: Microsoft’s famous (infamous? Notorious?) Local Administrator Password Solution. Chances are, you’re already using it, so I’ll cut to the chase:
What:
LAPS is an application designed to increase security by setting complex, unique passwords for each of the local admin accounts on domain-joined computers. These passwords are stored on the computer in Active Directory (AD), in a confidential attribute in the computer’s AD object, and rotated automatically according to password policy / expiry. Domain admins can give certain users read-only access to passwords when they need to log in to a local admin account.
The password-management tasks described above (setting, rotating, storing, etc.) are performed by a Group Policy Client-Side Extension (CSE) installed on each device.
Why:
Believe it or not; it’s still commonplace for companies to use an identical password for each local admin account in the domain (alarm bells? Yes, I hear them too). Doing so makes Pass-the-Hash (PtH) attacks and lateral privilege escalation – the tactic of expanding from the first compromised account to more accounts of the same privilege-level – an easy feat for hackers.
Thus: the need for LAPS.
Break Glass
The Break Glass Account: newest addition to Admin By Request’s Windows feature family.
What:
Break Glass is a feature built-in to Admin By Request’s PAM solution which aims to increase security by allowing IT admins to generate a temporary, one-time-use, Just-In-Time local admin account on an endpoint, on an as-needed basis.
The username and password for a Break Glass Account are automatically generated for each account, with complex and unique passwords stored in the web application, and accessible to administrators – who can then send the credentials via SMS (or other means) to the appropriate user.
When generating, the IT admin can set an expiry time for each account (between 15 minutes and an unlimited amount of time). Once generated, a Break Glass Account must be used (i.e., logged in to) within one hour, or is automatically terminated. Similarly, it will terminate automatically when it reaches its pre-configured expiry time.
Why:
Well, to put it bluntly: to fill in the security holes left by LAPS, while providing the same (and additional) functionality; taking the necessary bits of the password manager and incorporating them into something safer, easier, and more useable.
Head-to-Head
Before we break down functionality, security, configuration, ease-of-use, and accessibility, here are the capabilities of our two contenders:
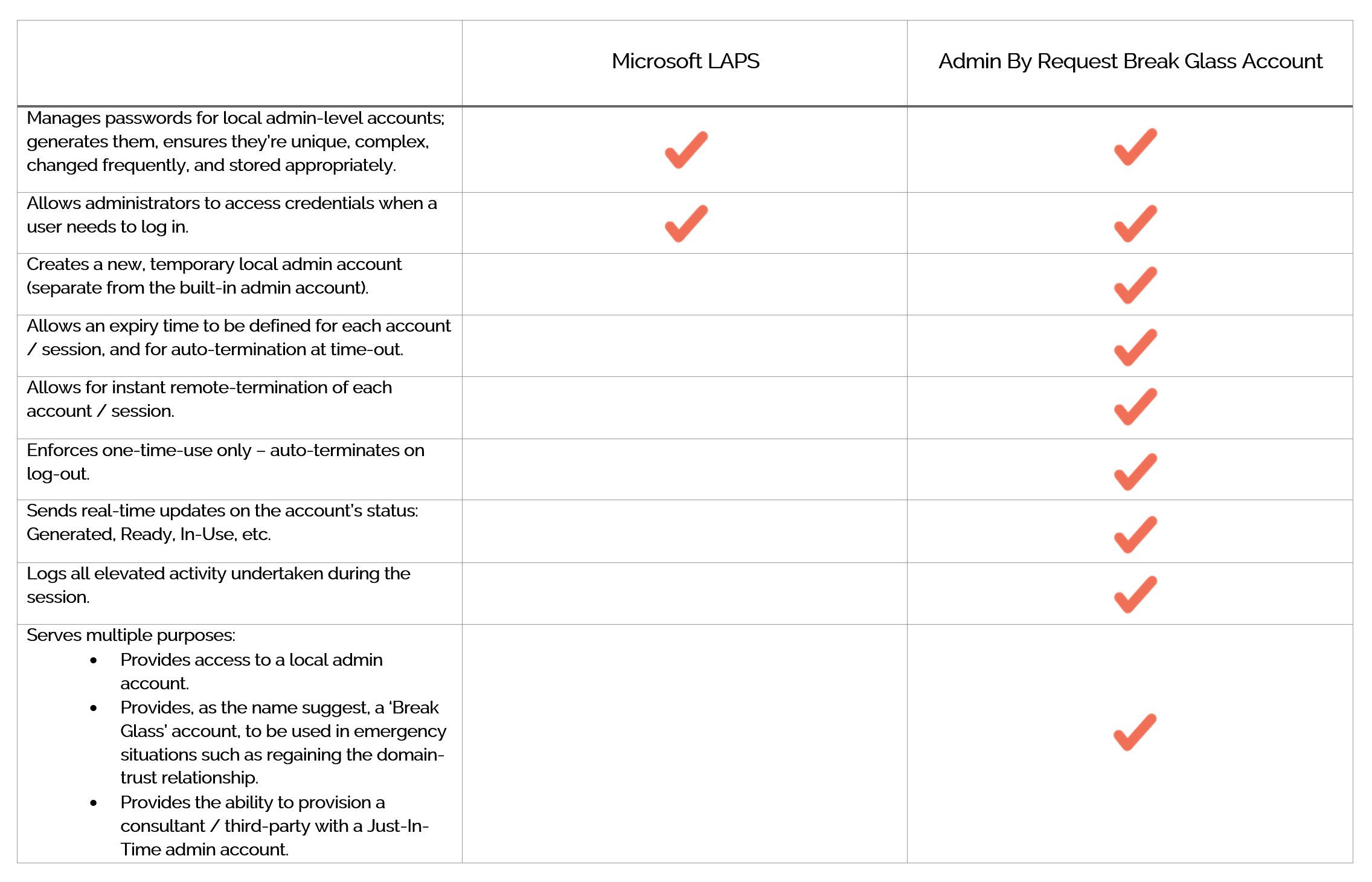
Comparison
Functionality
LAPS
When it comes to functionality, LAPS is very one-dimensional: it truly does the single thing that it sets out to do. Great. But there’s decent chunk of configuration involved (more on that later – see the Configuration section) for a simple password manager.
Break Glass
With Break Glass, we added some extra ‘uses’ to give you more bang for your buck. It solves the core problem that LAPS seeks to solve (protecting local admin accounts), while adding the additional security feature of Auditing all privileged activity that occurs during the session (more on this in the Security section); but it does more than just protection, providing workarounds useful in other common scenarios (see table above).
Security
Both solutions have the password rules down pat, but there’s a lot more to adequate security than just passwords.
LAPS
The solution is thorough enough with password management but falls short in one area: storage. LAPS stores the password on the client side, in a *confidential* attribute within the computer account in AD – on the computer that it belongs to. An article we published in Infosec magazine a few years back springs to mind:
“When not configured correctly, the software [LAPS] can create more problems than it solves. This is because administrator passwords are stored in plain text along with the AD computer record. TechGenix appropriately describes this as, “the digital equivalent of writing the password on a sticky note and placing it on the monitor”. If users with extended permissions are not removed and the appropriate groups not created, unintended users may have access to read the password property.”
Then there’s the potential for reverse-engineering, the use of key-gen software / cracks, and other ungodly hacker-tactics to obtain passwords stored on the client side. The vulnerability is there, just waiting to be exploited.
We will give 1 point to LAPS for it’s client-side password-storage: this method provides the ability to still access local admin accounts if the device is offline. But this small blessing is more trouble than it’s worth; any users who know of this workaround could use it to their advantage – by learning their password, disconnecting from the network, and retaining admin rights indefinitely (well, until they get caught).
Break Glass
The Break Glass account has password-protection measures in place (unique, complex, stored on the server side so impervious to key-gens and the like), however, passwords aren’t the focus. Instead, Break Glass essentially ‘skips the middleman’ and goes straight to the heart of the problem: the account itself. Forget fiddling around with password policies, AD storage, gaining access – manage the whole account, and have the password issue covered in the process.
The Break Glass Account eliminates the need – and constant risk – of having your built-in local admin accounts enabled. With the feature providing one-time-use local admin access on a Just-In-Time basis, you can permanently disable the built-in local Admin – minimizing the attack surface and window, and limiting the potential for compromise.
Because Break Glass is an additional feature of Admin By Request’s existing PAM solution, each account comes with the core Auditing security feature enabled. Any elevated activity performed by the user during a Break Glass session is logged in the User Portal Auditlog.
Configuration and Ease-of-Use
LAPS
Installation and configuration of LAPS isn’t the worst as far as configs go, but there are still a few finicky things to tick off before you can confidently rely on the software:
- All endpoints – both management devices and clients to be managed – require installation of a Group Policy Client-Side Extension.
- The AD schema needs to be extended to enable your systems and network to accommodate the application.
- Password settings such as complexity, length, and expiry need to be set.
- AD Access permissions need to be updated.
- Group Policy needs to be configured.
If steps 4 and 5 aren’t undertaken with the utmost attention to detail, you’ll be causing more problems than solving them by potentially giving the wrong access to users.
As for ease-of-use, LAPS loses points by requiring systems be on the domain in order to work.
Break Glass
Configuration? There is none. It comes built-in, pre-configured, and ready to roll; simply log in to your User Portal, navigate to Settings > click the desired endpoint > select Break Glass from the left-hand menu, and use the feature.
In terms of ease-of-use – it’s as easy as clicking a button. Literally. The feature is simple, intuitive, and you don’t need to be a super-tech-nerd to operate it. The fact that it’s combined into a single security software package means you don’t have to manage multiple security solutions on different platforms or through different applications.
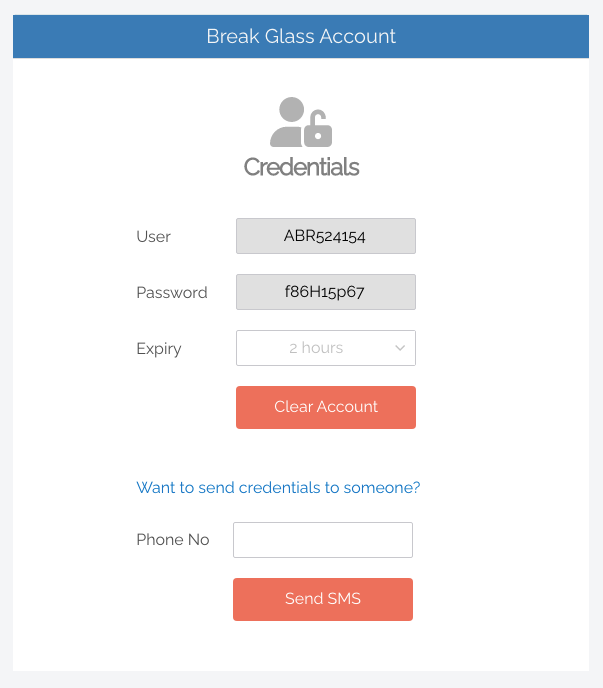
Possibly the best pro for ease-of-use is that the Break Glass Account does not require a domain; it works on domains, Azure AD, and stand-alone.
For more info on Break Glass Configuration, how to use it, and scenarios for use, check out our documentation page.
Accessibility
LAPS
Is accessible – and it’s free of charge (props to Microsoft). But as we know, it needs to be installed practically everywhere in order to cover all bases and is reliant on domains. As for who can access; that’s reserved for Domain Admins only.
Break Glass
Comes with Admin By Request’s PAM solution, so if you’ve got that, you’ve got Break Glass. If you’re not an existing user, you can download it for up to 25 endpoints, 100% free of charge. In terms of who can access and use the feature: anyone with User Portal credentials. And it’s probably a good time to mention that the next step for Break Glass is to make it available on all operating systems: macOS in Q2, and Linux in Q3.
TL, DR?
LAPS does its job adequately, is fairly simply to configure and use, but falls short in the security department. Break Glass solves the same problem, adds functionality, and covers all bases in the security department.
So, there it is: LAPS vs. Break Glass, stating the facts and nothing but. Granted, it’s a little skewed in our favor, but hey – that’s because we’ve created something cool, and we want to share it. Don’t take our word for it entirely – download a free plan of Admin By Request today and try it out yourself.







